The DE Bill, or, How I Learned to Stop Worrying and Love Tor

Andrew Bolster
Senior R&D Manager (Data Science) at Black Duck Software and Treasurer @ Bsides Belfast and NI OpenGovernment Network
Folks, we’re basically screwed; The Digital Economy Bill recieved Royal Accent on April 9th and is officially now Law.
So after barely three days of parliamentary ‘debate’ where only 20-ish MP’s actually spoke on the subject (but somehow 189 MP’s decided it was a good idea anyway), our civil rights have been sacrificed infront of the alter of copyright.
Many sites have a much more indepth tretise on the subject than I could do so I’ll keep this short.
Churchill said this about the rise of Socialism in Europe during WWII:
“The stations of uncensored expression are closing down; the lights are going out; but there is still time for those to whom freedom and parliamentary government mean something, to consult together.”
Anyway, no point in whining, time to do something about it.
How to use TOR to anonymise your internet traffic in Ubuntu
Tor is free software and an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world
Nice and easy, step 1, add the repository to your
/etc/apt/sources.list
deb http://deb.torproject.org/torproject.org $DISTRIBUTION main
In my case, $Distribution was karmic, for a full list of available distributions, check here
Grab the gpg key and update the apt-cache, and install:
gpg --keyserver keys.gnupg.net --recv 886DDD89
gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
sudo apt-get update
sudo apt-get install tor tor-geoipdb
So that’s tor installed, and you can act as a tor node, sharing your bandwidth to protect the anonymity of others (To mess with this, check out Tor’s guide). But to actually take advantage of it yourself, there’s more steps;
1) Polipo: A web caching proxy that should speed things up considerably while lightening the load on the Tor network. Normally just a simple apt-get install polipo, then grab the Tor Project’s polipo configuration and put it in either
/etc/polipi/config
or
~/.polipo
.
Finally, tidy everything up with a sudo service polipo restart
2) Use it: Either point your regular browser to HTTP proxy through
localhost:8118
(Polipo), or for SOCKS applications like IM and socket applications, go directly to the tor service at
localhost:9050
, Although depending on your system configuration, this could be a bad idea if you’re really paranoid.
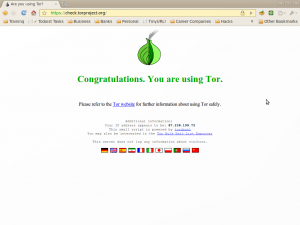
3) Test it. Heres how it looks when Tor is not configured properly.
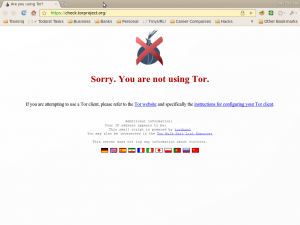
And heres how it is when it works!
There are a million and one ways of organising Tor, but Google and find the solution that works for you. For Firefox I recommend FoxyProxy, and Proxy Switchy for Chrome